Simply dragging files to the trash or formatting a hard drive is not enough to protect your sensitive information. With readily available data recovery software, supposedly deleted files, from confidential business strategies and client records to personal financial data, can be easily retrieved from discarded drives. This vulnerability creates significant risks, including identity theft, corporate espionage, and severe financial penalties for non-compliance with data protection regulations. True data security demands that the information is rendered permanently and irretrievably gone.
For any organization, from a small business to a large enterprise, understanding the most effective and secure methods for data destruction is a critical component of risk management. For organizations adhering to robust information security practices, understanding requirements like those outlined in ISO 27001 global standards is essential for maintaining a secure data lifecycle. Failing to properly sanitize media before disposal can lead to a catastrophic data breach.
This comprehensive guide is designed to provide clear, actionable insights into the best ways to destroy a hard drive. We will move beyond theory and delve into the practical applications, pros, cons, and specific use cases for eight industry-leading techniques. You will learn about everything from advanced software-based wiping and cryptographic erasure to complete physical obliteration through shredding and incineration. This list will equip you with the knowledge to select the appropriate destruction method based on your security needs, budget, and compliance obligations, ensuring your digital footprint is securely and permanently erased.
1. DBAN (Darik's Boot and Nuke)
DBAN, which stands for Darik's Boot and Nuke, is a powerful and widely recognized open-source utility designed for one purpose: to securely and permanently erase all data from a hard drive. Unlike simply deleting files, DBAN overwrites the entire drive with pseudorandom data, making the original information practically impossible to recover. This process is often called data sanitization or secure wiping.
Because DBAN is a self-contained program that boots from a USB drive or CD, it operates independently of the computer's installed operating system. This makes it an ideal solution for wiping drives in computers that are no longer functional or for sanitizing drives before a system is decommissioned, sold, or recycled.
How DBAN Works and When to Use It
DBAN implements several industry-standard sanitization methods. When you run the program, you can choose from various algorithms, each involving multiple passes of writing new data over the old. This is one of the best ways to destroy a hard drive's data without physically damaging the hardware itself, preserving its potential for reuse.
Use DBAN in these scenarios:
- Preparing for Resale or Donation: Securely erasing personal or business data from a computer before giving it away or selling it.
- Large-Scale IT Decommissioning: IT departments often use DBAN to sanitize dozens or hundreds of hard drives from retired workstations and servers before disposal.
- Compliance Requirements: For organizations that need to prove data has been securely erased but plan to reuse the hardware, DBAN provides a reliable software-based solution.
Key Insight: DBAN is highly effective for traditional magnetic hard disk drives (HDDs). However, it is not recommended for solid-state drives (SSDs) due to the way SSDs manage data with wear-leveling algorithms. Using DBAN on an SSD can degrade its lifespan without guaranteeing a complete wipe.
Actionable Tips for Using DBAN
To ensure a successful and safe wipe, follow these practical steps:
- Isolate the Target Drive: Before you begin, physically disconnect any external hard drives, network drives, or internal drives that you do not want to erase. DBAN will wipe any drive it detects, and a mistake is irreversible.
- Create Bootable Media: You will need a separate, functioning computer to download the DBAN ISO file and use a tool like Rufus or BalenaEtcher to create a bootable USB drive.
- Verify Drive Recognition: Once you boot into the DBAN interface, carefully check the list of detected drives to confirm the correct one is selected before starting the process.
- Allocate Ample Time: A secure wipe can take many hours, even days, depending on the drive's size and the chosen method. Do not interrupt the process once it has started.
For those preparing a machine for responsible disposal, understanding the full sanitization process is crucial. You can learn more about how to wipe a computer before recycling to ensure your data is handled correctly.
2. Physical Hard Drive Shredding/Destruction
Physical hard drive shredding is the ultimate method for data destruction, ensuring that information is completely and permanently unrecoverable. This industrial process involves feeding hard drives into specialized, high-powered shredders that grind and pulverize the entire device, including the platters, electronics, and casing, into small, unrecognizable pieces of metal and plastic. Unlike software-based wiping, shredding leaves no room for error or data recovery attempts.
This method is the gold standard for organizations with zero tolerance for data breaches, as it provides absolute certainty that the data is gone forever. By physically destroying the medium on which the data resides, shredding eliminates the drive itself, making it one of the most secure and best ways to destroy a hard drive permanently.
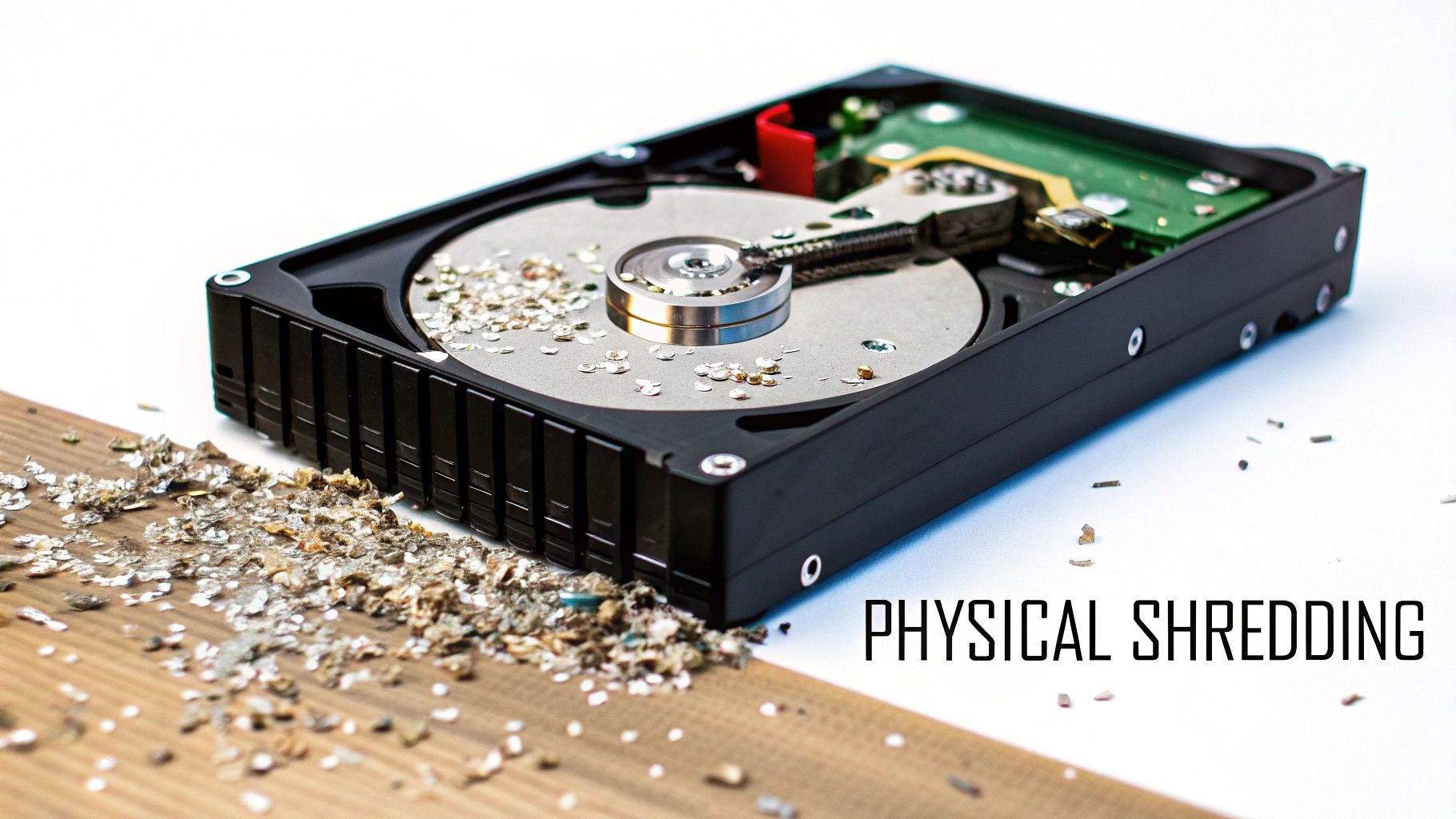
How Hard Drive Shredding Works and When to Use It
Professional data destruction services use industrial shredders designed specifically for electronic media. These machines can tear through both traditional HDDs and modern SSDs, reducing them to fragments that meet specific size requirements set by regulations like NAID AAA Certification. This process is often performed on-site using mobile shredding trucks or at a secure off-site facility.
Use hard drive shredding in these scenarios:
- Compliance with Strict Regulations: Healthcare organizations bound by HIPAA, financial institutions, and government agencies must use physical destruction to guarantee data sanitization and avoid severe penalties.
- End-of-Life Asset Management: For enterprises and data centers decommissioning large volumes of drives that will not be reused, shredding is the most efficient and secure disposal method.
- Protecting Sensitive Intellectual Property: Businesses with proprietary data, trade secrets, or sensitive customer information use shredding to eliminate any risk of corporate espionage.
Key Insight: Physical destruction is the only method approved by the NSA for top-secret data on hard drives. It is equally effective on both HDDs and SSDs, as it completely destroys the physical storage components, bypassing the complexities of SSD data architecture that challenge software-wiping tools.
Actionable Tips for Using Shredding Services
To ensure a secure and compliant destruction process, follow these best practices:
- Choose a Certified Provider: Partner with a company that holds certifications like R2 (Responsible Recycling) or is NAID AAA Certified. These certifications ensure adherence to strict security and environmental standards.
- Request a Certificate of Destruction: Always obtain a formal Certificate of Destruction upon completion. This document serves as a legal audit trail, proving your organization complied with data protection laws.
- Verify Chain of Custody: Ask the provider about their chain of custody procedures, which track your assets from the moment they leave your possession until they are destroyed.
- Witness the Destruction: Whenever possible, opt for on-site shredding services where you can personally witness the drives being destroyed, providing absolute peace of mind.
For organizations needing a reliable and compliant solution, professional services are essential. You can find more details about professional shredding services for hard drives to ensure your data is handled with the utmost security.
3. Degaussing (Magnetic Erasure)
Degaussing is a method of data destruction that uses a powerful magnetic field to completely neutralize and randomize the magnetic orientation of particles on a hard drive's platters. This process instantly and permanently erases all stored data, effectively rendering the hard drive's contents unreadable and the drive itself unusable. It is a highly effective method for sanitizing magnetic media like traditional hard disk drives (HDDs) and magnetic tapes.

Unlike software-based wiping, which overwrites data, degaussing attacks the fundamental magnetic properties where data is stored. The powerful pulse from a degausser scrambles the magnetic domain, essentially resetting the drive to a completely blank state with no trace of the original information. This makes it one of the best ways to destroy a hard drive’s data when dealing with high-security information.
How Degaussing Works and When to Use It
A hard drive is passed through the intense magnetic field of a degausser, a specialized piece of equipment. This field is strong enough to overcome the drive’s own magnetic coercivity, which is its resistance to demagnetization. The process is extremely fast, often taking less than a minute per drive, making it ideal for high-volume data destruction requirements.
Use Degaussing in these scenarios:
- Government and Military Data: The U.S. National Security Agency (NSA) and Department of Defense (DoD) approve degaussing for destroying classified magnetic media.
- High-Volume Data Centers: Organizations needing to dispose of hundreds or thousands of HDDs quickly find degaussing more efficient than software wiping.
- Financial and Healthcare Institutions: Banks and hospitals use degaussing to sanitize backup tapes and hard drives containing sensitive financial or patient information.
Key Insight: Degaussing is only effective on magnetic storage media like HDDs and tapes. It has no effect on solid-state drives (SSDs), flash drives, or optical media (CDs/DVDs), as they do not store data magnetically. Attempting to degauss an SSD will not erase its data.
Actionable Tips for Using Degaussing
To properly sanitize a drive and ensure compliance, follow these best practices:
- Use an Approved Degausser: Ensure the degausser is listed on the NSA's Evaluated Products List (EPL) and has a magnetic field strong enough for modern high-coercivity hard drives.
- Remove the Drive from Casing: For maximum effectiveness, remove the hard drive from its computer tower, server chassis, or external enclosure before processing.
- Verify Destruction: After degaussing, the drive's firmware is often destroyed, making it inoperable. It should not be able to spin up or be recognized by a computer. For added security, many organizations physically destroy the drive after degaussing.
- Document Everything: Maintain a log of each drive's serial number, the date of degaussing, and the operator's name to create an auditable record of destruction.
Degaussing is a core component of a comprehensive data destruction strategy. You can explore a complete overview of what data sanitization is to understand how it fits into your security protocols.
4. ATA Secure Erase
ATA Secure Erase is a powerful, firmware-based command built directly into modern ATA and SATA hard drives, including both traditional hard disk drives (HDDs) and solid-state drives (SSDs). Unlike software-based wiping tools that write new data over old, this command triggers the drive's internal controller to reset all storage blocks to their original, "clean" factory state. This process effectively and rapidly erases all user data stored on the drive.
Because the command is executed by the drive's own hardware, it is often much faster and more thorough than external software solutions. It's an exceptionally efficient method for sanitizing drives because it bypasses the operating system entirely and addresses the physical storage directly, which is one of the best ways to destroy a hard drive's data while preserving the hardware for reuse.
How ATA Secure Erase Works and When to Use It
When initiated, the ATA Secure Erase command instructs the drive's firmware to apply a voltage spike to all NAND cells (in an SSD) or overwrite the entire data area (in an HDD). This process is designed to be irreversible and meets compliance standards set by organizations like the National Institute of Standards and Technology (NIST).
Use ATA Secure Erase in these scenarios:
- Upgrading or Replacing Drives: When you are upgrading to a larger or faster drive and want to securely wipe the old one for reuse, donation, or sale.
- Enterprise IT Asset Management: IT departments use this method to quickly sanitize drives from retired laptops and workstations before redeploying them internally.
- Restoring SSD Performance: For SSDs, performing a secure erase can sometimes restore the drive to near-factory performance levels by clearing all cells.
Key Insight: ATA Secure Erase is one of the most effective and recommended methods for wiping SSDs. Unlike software overwriting tools that can cause unnecessary wear and may not erase all data due to features like over-provisioning, the firmware-level command ensures a complete and safe sanitization.
Actionable Tips for Using ATA Secure Erase
To correctly execute this command and ensure complete data removal, follow these best practices:
- Check for Compatibility: Before you start, confirm that your specific drive model supports the ATA Secure Erase command. This information is usually available on the manufacturer's website or in the drive's technical specifications.
- Use Manufacturer-Specific Tools: The most reliable way to issue the command is through the manufacturer's own utility, such as Seagate's SeaTools or Western Digital's Dashboard. Alternatively, utilities like Parted Magic can also access this function.
- Ensure a Direct SATA Connection: For the command to work properly, the drive should be connected directly to a motherboard's SATA port. USB-to-SATA enclosures or adapters can often block the command.
- Backup and Verify: Always back up any data you wish to keep before initiating the process. Once the command is executed, the data is gone forever. Some tools provide a verification step to confirm the wipe was successful.
For organizations needing to manage multiple drives, understanding the nuances of different data destruction methods is critical. You can learn more about how ATA Secure Erase fits into a broader strategy for secure hard drive disposal to ensure compliance and data security.
5. Thermal Destruction/Incineration
Thermal destruction, or incineration, is one of the most absolute methods for ensuring data is permanently irrecoverable. This process involves subjecting hard drives to extreme temperatures, often exceeding 1,000°C (1,832°F), in a controlled industrial incinerator. The intense heat melts and vaporizes the drive's platters, circuitry, and casing, completely destroying the physical medium on which data is stored and making any form of data recovery impossible.
This method goes beyond simple damage; it fundamentally alters the material state of the hard drive. Because of its finality and environmental impact, incineration is typically reserved for the highest security classifications where the cost and complexity are justified by the need for complete and verifiable data annihilation. It is a powerful tool in the arsenal of the best ways to destroy a hard drive permanently.
How Incineration Works and When to Use It
Incineration works by leveraging extreme heat to destroy the physical integrity of the hard drive. For a foundational understanding of how fire works, including its essential components, you can explore information about the fundamental components of fire to appreciate the science behind this destructive process. This method ensures that the magnetic platters of an HDD or the NAND flash chips of an SSD are reduced to ash and slag.
Use Thermal Destruction in these scenarios:
- Top-Secret Government and Military Data: For destroying classified materials where national security is at stake and no trace of the data can be allowed to survive.
- Highly Sensitive Corporate R&D: Companies protecting invaluable trade secrets or proprietary research may opt for incineration to prevent any possibility of corporate espionage.
- High-Stakes Compliance: Certain financial or healthcare institutions with extremely sensitive records may use this method to meet the most stringent data destruction requirements.
Key Insight: Thermal destruction is the ultimate failsafe for data sanitization. Unlike other methods, it leaves no physical media to analyze or attempt recovery from. However, it is an environmentally intensive process that requires specialized facilities and adherence to strict regulations.
Actionable Tips for Using Thermal Destruction
Engaging in thermal destruction requires careful planning and partnership with certified professionals. Use these steps to ensure the process is secure, compliant, and responsible:
- Partner with Certified Facilities: Only work with e-waste recyclers or data destruction companies that are certified for high-temperature incineration and can provide a full chain of custody.
- Request a Certificate of Destruction: Always obtain detailed documentation, including serial numbers of the destroyed drives, that serves as legal proof of destruction for compliance and auditing purposes.
- Verify Environmental Permits: Ensure the facility holds all required local and federal environmental permits for operating an incinerator to avoid legal and reputational risks associated with improper disposal.
- Assess Environmental Impact: Discuss the facility's process for managing emissions and waste byproducts. Inquire about any available carbon offset programs to mitigate the environmental footprint of the process.
6. SSD Secure Erase and TRIM Operations
Unlike traditional hard drives, Solid-State Drives (SSDs) require a different approach for secure data destruction. Using overwrite methods like DBAN is ineffective and can damage the drive. Instead, SSDs have a built-in command set, including Secure Erase and TRIM, designed specifically to reset the drive to a factory-fresh state, making it one of the best ways to destroy a hard drive's data at the firmware level.
Secure Erase is a command that tells the SSD’s controller to flush all stored electrons in its NAND flash memory cells, effectively resetting every block of data. This process leverages the drive's internal architecture to ensure data is thoroughly and irreversibly cleared. The TRIM command complements this by allowing the operating system to inform the SSD which data blocks are no longer in use, making the cleanup process more efficient.
How SSD Secure Erase Works and When to Use It
SSD Secure Erase is a software-based command initiated through the drive manufacturer's utility software or sometimes directly from the computer's BIOS/UEFI. This command triggers an internal, firmware-level process that erases all user data by applying a voltage spike to the NAND flash memory, returning the cells to their original, empty state. This method preserves the drive's health and performance for future use.
Use SSD Secure Erase in these scenarios:
- Re-purposing or Selling an SSD: Before selling, donating, or re-purposing an SSD for another use, this method ensures all previous data is completely unrecoverable.
- Restoring SSD Performance: Over time, an SSD's performance can degrade. A Secure Erase can restore it to near-factory performance levels.
- IT Asset Disposition: For IT departments decommissioning systems with SSDs, using manufacturer tools is the standard procedure for data sanitization when the drives are intended for reuse or resale.
Key Insight: Standard data wiping software designed for HDDs is not suitable for SSDs. The wear-leveling algorithms in SSDs distribute data across memory cells to prolong drive life, meaning overwriting tools can miss data blocks and cause unnecessary wear without guaranteeing complete erasure. Always use the manufacturer's specific utility.
Actionable Tips for Using SSD Secure Erase
To correctly perform a secure erase and protect your data, follow these best practices:
- Use Manufacturer-Specific Tools: Always download the official utility from your SSD's manufacturer, such as Samsung Magician, Intel SSD Toolbox, or Crucial Storage Executive. These tools are designed to work perfectly with their specific firmware.
- Back Up Everything First: This process is final and irreversible. Ensure any data you wish to keep is securely backed up on a separate device before you begin.
- Ensure the Drive is a Secondary Drive: Most utilities require the SSD to be connected as a secondary, non-OS drive to perform the erase. You may need to connect it to another computer or boot from a different drive.
- Verify Completion: After the process finishes, the software will provide a confirmation message. Trusting this confirmation is key to knowing the data is gone.
Properly erasing an SSD is a critical step in secure data management. You can learn more about how to destroy a hard drive before disposal to understand all available options for both SSDs and HDDs.
7. Multi-Pass Overwriting (Gutmann Method and Variants)
Multi-pass overwriting is a highly intensive software-based data destruction method that involves writing new patterns of data onto every sector of a hard drive multiple times. The most famous of these techniques is the Gutmann method, which performs 35 distinct passes. This extreme approach was designed to make data recovery theoretically impossible, even with advanced laboratory tools like magnetic force microscopy that could potentially detect residual magnetic traces on older drive platters.
This method goes far beyond a standard single-pass wipe by using a complex sequence of random and specific patterns in its overwriting process. It was developed based on the encoding technologies used in older MFM/RLL hard drives. For organizations with extreme security requirements or those decommissioning very old hardware, a multi-pass overwrite represents one of the most thorough ways to destroy a hard drive's data electronically without any physical interaction.
How Multi-Pass Overwriting Works and When to Use It
The core principle of a multi-pass overwrite is to completely obliterate the magnetic "ghost" of the original data. By writing a specific series of patterns over the same physical location on a drive platter, any lingering magnetic residue is randomized to the point of being unreadable. While the full 35-pass Gutmann method is often overkill for modern drives, variants using 3 or 7 passes (like the DoD 5220.22-M standard) provide a high degree of security.
Use multi-pass overwriting in these scenarios:
- High-Security Data Sanitization: Government agencies, defense contractors, and financial institutions may use this method to comply with strict internal data destruction policies for non-classified data.
- Wiping Older Magnetic Drives: This technique is most relevant for legacy HDDs where concerns about advanced forensic recovery are highest.
- Verifiable Software Destruction: When physical destruction is not an option but the highest level of data sanitization assurance is required for hardware that will be reused.
Key Insight: The Gutmann method was designed for obsolete hard drive technologies. For modern HDDs and especially SSDs, a single-pass overwrite (writing all zeros or random data) is typically sufficient. The complexity and time of a 35-pass wipe provide no significant security benefit on today's hardware and can cause unnecessary wear.
Actionable Tips for Using Multi-Pass Overwriting
To effectively use this data destruction technique, careful planning and execution are essential:
- Choose the Right Tool: Utilize trusted software like DBAN, Eraser, or various Linux utilities (like
shred) that specifically offer multi-pass algorithms. Select the appropriate method based on your security needs, such as a 3-pass DoD wipe or the full Gutmann. - Start with Fewer Passes: For most business applications, a 3 to 7-pass overwrite provides more than adequate security and takes significantly less time than 35 passes. Assess your risk profile to determine the appropriate level.
- Schedule for Off-Hours: A multi-pass overwrite is extremely time-consuming and resource-intensive. Run the process overnight or during a weekend to avoid impacting system availability and to ensure it can complete without interruption.
- Monitor Drive Health: The intense read/write activity of a multi-pass wipe can put significant stress on a hard drive. For older drives, there is a risk of hardware failure during the process. Monitor the process and be prepared for this possibility.
8. Encryption Before Disposal (Cryptographic Erasure)
Cryptographic erasure, or crypto-erase, is a highly effective data sanitization method where a hard drive's data is rendered permanently unreadable by destroying its encryption key. Instead of overwriting or physically damaging the drive, this approach leverages the power of strong, full-disk encryption. Once the unique key used to encrypt the data is securely deleted, the information on the drive becomes a mass of scrambled, indecipherable characters with no way to unlock it.
This method is one of the best ways to destroy a hard drive's data because it is fast, efficient, and can be performed remotely. It is particularly valuable for modern drives like SSDs and self-encrypting drives (SEDs), where traditional overwriting methods can be less effective or even detrimental to the hardware's lifespan.

How Cryptographic Erasure Works and When to Use It
The principle behind crypto-erasure is simple: the security of the data is tied directly to the encryption key. By implementing full-disk encryption before any sensitive data is written, the drive is protected from day one. When the time comes for disposal, the only action needed is to securely and irretrievably delete the key. The encrypted data remains on the drive, but without the key, it is computationally infeasible to recover.
Use Cryptographic Erasure in these scenarios:
- Decommissioning Self-Encrypting Drives (SEDs): Enterprise-grade SEDs are built for this purpose, allowing for instant and secure sanitization by destroying the onboard media encryption key (MEK).
- Managing Mobile Devices and Laptops: Operating systems like macOS (FileVault) and Windows (BitLocker) use built-in full-disk encryption, making crypto-erasure a standard part of their security architecture.
- Cloud and Data Center Environments: In large-scale virtualized environments, destroying encryption keys is a fast and efficient way to sanitize data from retired storage arrays without physical access.
- Compliance with Data Privacy Regulations: NIST Special Publication 800-88 recognizes cryptographic erasure as a valid and secure form of data sanitization when implemented correctly.
Key Insight: The effectiveness of cryptographic erasure depends entirely on the strength of the encryption and the complete, verifiable destruction of the key. If the key is ever compromised or backed up insecurely, the data remains vulnerable.
Actionable Tips for Using Cryptographic Erasure
To implement this method securely, follow these best practices:
- Encrypt from the Start: Enable full-disk encryption (like BitLocker, FileVault, or LUKS) on all devices before they are put into service. This proactive step ensures all data stored is protected from day one.
- Manage Keys Securely: Store encryption keys in a secure, separate location from the physical hardware. Use a dedicated key management system (KMS) for enterprise environments.
- Verify Key Destruction: Implement and document a formal procedure for destroying encryption keys. This process must be irreversible and verifiable to meet compliance standards.
- Combine with Physical Destruction: For maximum assurance, especially with highly sensitive data, combine cryptographic erasure with physical destruction. After the key is deleted, the drive can be shredded or crushed to eliminate all risks.
8 Hard Drive Destruction Methods Compared
| Method | Implementation Complexity 🔄 | Resource & Cost ⚡ | Effectiveness & Expected Outcome ⭐📊 | Ideal Use Cases 📊 | Key Advantages 💡 |
|---|---|---|---|---|---|
| DBAN (Darik's Boot and Nuke) | Moderate–High: create bootable media; technical steps | Low cost (free); time‑intensive for large drives | ⭐⭐⭐⭐ — Very effective on HDDs; slow; not ideal for SSDs | IT decommission, resale/donation of HDDs | Free, OS‑independent; works on non‑booting systems |
| Physical Hard Drive Shredding/Destruction | Low for user: outsource to vendor | High per‑drive cost; transport and logistics | ⭐⭐⭐⭐⭐ — Irreversible physical destruction; certification available | Regulated industries, bulk disposals, strict compliance | Guaranteed non‑recoverability; certified documentation |
| Degaussing (Magnetic Erasure) | Medium: specialized equipment or vendor | High equipment/vendor cost; fast throughput | ⭐⭐⭐⭐ — Instant for magnetic media; ineffective for many SSDs/encrypted drives | Legacy magnetic media, tapes, bulk data center sanitization | Rapid, non‑invasive for magnetic media; handles damaged drives |
| ATA Secure Erase | Low–Medium: firmware command; drive must be recognized | Low cost; minutes per drive | ⭐⭐⭐⭐ — Fast and reliable on supported modern drives; vendor variations exist | Modern HDDs/SSDs in enterprise and consumer environments | Firmware‑level, fast, minimal wear; manufacturer‑supported |
| Thermal Destruction / Incineration | Low for user: vendor operated; strict regulations | Very high cost; environmental impacts | ⭐⭐⭐⭐⭐ — Complete destruction to ash; highest assurance | Top‑secret/classified disposals, highest regulatory needs | Absolute irrecoverability; compliance with strict standards |
| SSD Secure Erase & TRIM | Low–Medium: manufacturer tools; drive must be functional | Low cost; extremely fast execution | ⭐⭐⭐⭐ — Best for SSDs; fast and efficient; some implementation gaps | Modern laptops, NVMe/SATA SSD maintenance and disposal | Fast, minimal wear, built into many SSDs; preserves reuse |
| Multi‑Pass Overwriting (Gutmann & variants) | Medium: run software for many passes; long runtimes | Moderate (time, electricity); no special hardware | ⭐⭐⭐ — Extremely thorough for old HDDs; overkill for modern encrypted drives | Older HDDs, extreme threat models, research settings | Scientifically designed patterns; no extra hardware needed |
| Encryption Before Disposal (Cryptographic Erasure) | High up front: implement and manage keys correctly | Low hardware cost; key management overhead | ⭐⭐⭐⭐ — Very effective if keys are securely destroyed; allows reuse | Reusable drives, enterprise workflows, continuous protection | Cost‑effective; enables secure resale/reuse; NIST‑recognized |
Your Next Step: Secure and Certified Data Destruction in Metro Atlanta
Choosing from the best ways to destroy a hard drive is not just a technical decision; it's a fundamental security and business strategy. Throughout this guide, we've explored a wide spectrum of methods, each with its own unique applications, strengths, and weaknesses. From software-based solutions like DBAN and multi-pass overwriting to the absolute finality of physical shredding and thermal destruction, the path to secure data sanitization is varied and complex.
We've seen that while a DIY approach using tools like ATA Secure Erase or cryptographic erasure can be effective for individual drives or smaller operations, it places the full burden of execution, verification, and liability squarely on your shoulders. The critical takeaway is that not all destruction methods are created equal, and the right choice depends entirely on your specific security requirements, regulatory obligations, and the type of media you are retiring.
Bridging Theory and Practical Application
The journey from understanding these methods to implementing them flawlessly can be fraught with risk. A single improperly wiped drive can lead to a catastrophic data breach, resulting in severe financial penalties, reputational damage, and loss of customer trust. This is where the distinction between knowing what to do and knowing how to do it with certified precision becomes paramount.
For organizations in healthcare, finance, education, or government sectors within the Metro Atlanta area, compliance is not optional. Regulations like HIPAA, SOX, and GDPR demand not just that data is destroyed, but that the destruction process is documented, auditable, and certified. This level of assurance is nearly impossible to achieve with consumer-grade tools or ad-hoc physical destruction.
Key Insight: The true value of professional data destruction lies not just in the act of destruction itself, but in the certified, auditable proof that it was done correctly, protecting your organization from future liability.
Why Professional Partnership is the Ultimate Security Measure
Ultimately, the most secure and efficient strategy for most businesses is to partner with a certified IT Asset Disposition (ITAD) specialist. This approach consolidates all the best practices we've discussed into a single, managed service. It removes the guesswork, eliminates the risk of human error, and provides the crucial documentation needed to satisfy any compliance audit.
Consider the advantages for your Metro Atlanta business:
- Guaranteed Compliance: Professionals use NIST and DoD-compliant methods and provide Certificates of Data Destruction, giving you a clear audit trail.
- Absolute Security: Commercial-grade shredders and degaussers offer a level of physical destruction that far exceeds what can be achieved with a drill press or hammer.
- Efficiency and Scalability: Whether you have ten hard drives or ten thousand, a professional service can handle the logistics, removal, and destruction process without disrupting your operations.
- Environmental Responsibility: Reputable vendors ensure that the decontaminated materials are recycled according to R2 or e-Stewards standards, aligning your security goals with corporate sustainability.
For businesses in Sandy Springs, Alpharetta, Marietta, and across the Metro Atlanta region, the decision is clear. Don't let retired IT assets become a ticking time bomb in a storage closet. By engaging a local, certified expert, you transform a potential liability into a securely closed chapter in your data's lifecycle. This proactive step is the final, and most important, part of mastering the best ways to destroy a hard drive.
Ready to ensure your company's data is destroyed with certified precision? Montclair Crew Recycling offers comprehensive, on-site, and off-site data destruction services for businesses throughout the Metro Atlanta area, providing the peace of mind that comes with professional and compliant IT asset disposition. Visit us online to schedule your service and secure your sensitive information today: Montclair Crew Recycling.
